Leading Features of the Best Cyber Security Services in Dubai You Should Know
Wiki Article
Checking Out Exactly How Cyber Security Works to Secure Your Online Presence
In today's digital landscape, shielding one's online existence has actually come to be increasingly essential, with cyber threats evolving at an alarming pace. Cyber safety and security employs a complex strategy, incorporating advanced modern technologies like firewall softwares, security, and multi-factor verification to protect delicate information. Exactly how do these technologies work with each other to produce a seamless shield against cyber hazards?Comprehending Cyber Hazards
In the electronic landscape, cyber risks stand for a formidable difficulty, requiring a nuanced understanding of their nature and potential effect. These threats encompass a vast array of harmful tasks orchestrated by individuals, teams, or perhaps nation-states, targeting sensitive data, interrupting procedures, or triggering reputational damages. Understanding cyber dangers starts with identifying the different types they take, including malware, phishing, ransomware, and distributed denial-of-service (DDoS) strikes.Malware, or harmful software program, consists of viruses, worms, and trojans that infiltrate systems to cause or steal data harm. Ransomware encrypts targets' data, requiring a ransom money for its release, positioning substantial functional and monetary threats.
Acknowledging the motivations behind these dangers is necessary. Cybercriminals commonly look for economic gain, while hacktivists may go after ideological goals. State-sponsored assaulters might target important infrastructure for espionage or destabilization functions. By thoroughly understanding the varied nature of cyber hazards, companies can much better prepare for potential vulnerabilities and tactically designate sources to boost their defenses versus these ever-evolving hazards.
Key Cyber Security Technologies
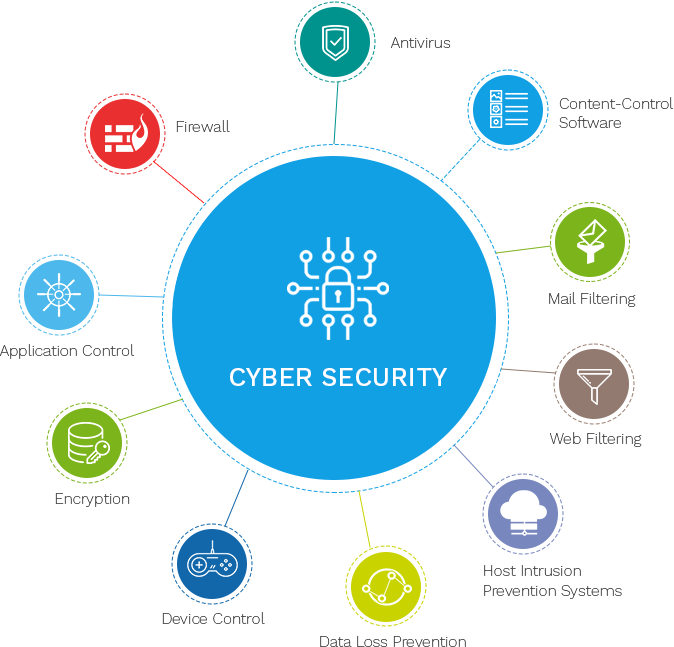
As organizations strive to guard their digital possessions, crucial cybersecurity innovations play an essential duty in strengthening defenses versus cyber risks. These technologies encompass a broad spectrum of tools and techniques made to protect information integrity, confidentiality, and schedule. In today's electronic landscape, breach discovery systems (IDS) and breach avoidance systems (IPS) are crucial. IDS display network traffic for dubious tasks, while IPS actively block potential threats, guaranteeing real-time protection.In addition, antivirus and anti-malware solutions remain essential in determining and alleviating malicious software program. They use heuristic and signature-based techniques to identify well-known and unknown hazards. Endpoint discovery and feedback (EDR) systems even more enhance security by giving thorough exposure right into endpoint activities, making it possible for quick case reaction.
Identity and gain access to monitoring (IAM) modern technologies make certain that just accredited customers get to critical sources, thus reducing the risk of unapproved information gain access to. Multifactor authentication (MFA) includes an added layer of safety, needing users to supply several confirmation factors.
In addition, safety information and event management (SIEM) systems accumulation and evaluate security information, providing understandings into possible vulnerabilities and facilitating aggressive risk management. These modern technologies collectively create a robust structure, equipping organizations to preserve a resistant cybersecurity pose.
Role of Firewalls and File Encryption
Firewalls and security are essential parts of a robust cybersecurity method, each serving an unique yet corresponding role in safeguarding electronic settings. Firewalls function as barriers between relied on inner networks and untrusted external entities. By controlling incoming and outbound network web traffic, they protect against unauthorized access to data and systems. Firewall softwares make use of predefined security policies to obstruct or allow information packages, efficiently protecting delicate details from cyber threats. They are the very first line of defense, filtering system web traffic and making certain only genuine communications are enabled.Security, on the various other hand, changes understandable data into an encoded layout that can just be figured out with a particular cryptographic secret. This process guarantees that information continues to be safe and secure and personal during transmission or storage. Even if obstructed, secured info is made ineffective to unauthorized users without accessibility to the decryption trick. Encryption is essential for protecting sensitive information such as economic data, personal recognition information, and proprietary service info.
Together, firewall programs and file encryption provide a thorough defense device. While firewall softwares manage accessibility and guard networks from unapproved entrance, security safeguards data honesty and confidentiality. Their incorporated application is important in mitigating threats and guaranteeing the protection of digital properties in an increasingly interconnected world.
Importance of Multi-Factor Authentication
While firewall programs and security create the foundation of cybersecurity, improving defenses even more requires the execution of multi-factor verification (MFA) MFA adds an extra layer of safety by calling for individuals to validate their identity via 2 or even more different elements before obtaining accessibility to delicate information or systems. These factors generally consist of something the customer understands (a password), something the user has (a protection token or smart device), and something the individual is (biometric confirmation such as a finger print or face recognition)The relevance of MFA in protecting on-line presence is vital in today's electronic landscape. With cyber risks coming to be increasingly advanced, relying only on traditional password-based authentication leaves systems at risk to breaches.
.jpg?width=1920&height=1080&name=Four%20Kinds%20of%20Cybersecurity%20Companies%20(1).jpg)
Behavioral Analytics in Cyber Security
Behavioral analytics stands for a pivotal development in cybersecurity, providing an innovative approach to threat detection and prevention. By evaluating patterns in individual actions, this visit this website technique recognizes anomalies that might suggest possible cyber threats.This innovation is especially efficient in spotting insider dangers and zero-day assaults, which are commonly missed out more information on by standard protection systems. Expert hazards, where people within a company misuse access benefits, can be particularly damaging and difficult to detect. Best Cyber Security Services in Dubai. Behavior analytics offers a layer of examination that can catch subtle inconsistencies in actions, such as uncommon gain access to patterns or data transfers, before they escalate into significant safety and security incidents
Furthermore, the vibrant nature of behavior analytics enables it to adapt to advancing threats, offering continual protection as cyberattack techniques change. As companies progressively count on digital frameworks, integrating behavioral analytics right into cybersecurity methods guarantees a resilient protection, safeguarding delicate data and keeping depend on in digital communications.
Conclusion
To conclude, the diverse approach of cyber protection, encompassing modern technologies such as firewall softwares, security, multi-factor authentication, and behavior analytics, plays an essential duty in safeguarding on-line presence. By filtering system traffic, protecting information transmission, needing numerous confirmation techniques, and monitoring individual task for anomalies, these modern technologies collectively attend to the intricacies of modern cyber threats. This layered protection not just safeguards economic and individual information however likewise ensures continuous security in an ever-evolving electronic landscape.
As organizations make every effort to secure their digital properties, crucial cybersecurity innovations play a vital role in strengthening defenses against cyber risks. Firewall programs use predefined security policies browse around this web-site to obstruct or allow data packages, efficiently securing sensitive details from cyber risks.This technology is especially reliable in identifying insider hazards and zero-day assaults, which are often missed by standard safety and security systems. By filtering system traffic, protecting data transmission, calling for multiple confirmation approaches, and keeping track of customer activity for anomalies, these modern technologies jointly resolve the complexities of modern-day cyber threats.
Report this wiki page